WannaCry Ransomware Attack
Submission 38,097
Part of a series on Ransomware. [View Related Entries]
Overview
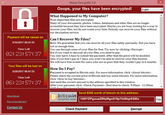
The Wannacry Ransomware Attack was a global Microsoft Windows cyber-attack infecting upwards of 230,000 computers, which demanded victims pay ransoms in bitcoin to have access to their machines.
Background
In mid-April 2017, the hacker group Shadow Brokers released a collection of NSA hacking tools online, including a tool named EternalBlue exploiting a weakness in Microsoft Windows' Server Message Block protocol. On April 21st, Ars Technica[1] reported that upwards of 107,000 computers were infected with the DoublePulsar[2] backdoor exploit tool. On May 12th, computers around the world were infected with the WannaCry ransomware program, which may have been executed through a spear phishing attack according to some researchers. When executed, the program initially checks a domain name as a "kill switch" before encrypting the user's data and demanding a ransom of approximately $300 USD in bitcoin within 72 hours or $600 within one week.

Developments
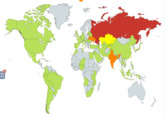
According to the European Union Agency for Law Enforcement Cooperation (Europol), WannaCry was unprecedented in scale compared other cyber attacks in history. In England and Scotland, the attack infected computers and medical devices at National Health Service hospitals, leading NHS to turn away all non-critical emergencies. According to the Russian multinational cybersecurity company Kaspersky Lab,[6] the largest number of the attacks occurred in Russia, Ukraine, India and Taiwan.

Online Reaction
On May 12th, Twitter published a Moments page titled "Cyber attack cripples UK hospitals, spreads to other countries."[7] In the coming days, several posts about the ransomware reached the front page of various subreddits, including /r/worldnews,[8] /r/YouShouldKnow[9] and /r/pcmasterrace.[10] Meanwhile, posts on 4chan referred to the attacks as "The Hackening."[11][12]
Kill Switch Discovery
According to an interview with The Guardian, Twitter user @MalwareTech[3] claimed to have discovered that the WannaCry malware was attempting to connect to a specific domain after hearing news reports about the cyber attack. He then registered the domain for $10.69, which immediately engaged the program's "kill switch," halting its spread.

On May 13th, MalwareTech published a blog post titled "How to Accidentally Stop a Global Cyber Attacks," explaining how engaging the kill switch was initially accidental.[4] Additionally, a video showing the spread of the program was uploaded to the MalwareTech YouTube channel (shown below).
On May 13th, The Hacker News[5] reported that variations of the ransomware had been discovered with different kill switch domains and some that did not contain a kill switch at all.
Park Jin-hyok
On September 6th, 2018, The United States Department of the Treasury announced that they had charged North Korean man Park Jin-hyok (shown below), an alleged North Korean operative, with involvement in the 2014 Sony Pictures Hack and the WannaCry ransomware attack.[13] In a statement, First Assistant United States Attorney Tracy Wilkison said:[14]
“The complaint charges members of this North Korean-based conspiracy with being responsible for cyberattacks that caused unprecedented economic damage and disruption to businesses in the United States and around the globe. The scope of this scheme was exposed through the diligent efforts of FBI agents and federal prosecutors who were able to unmask these sophisticated crimes through sophisticated means. They traced the attacks back to the source and mapped their commonalities, including similarities among the various programs used to infect networks across the globe.”

According to FastCompany,[14] Park worked with the hacking group "sometimes referred to as the Lazerous Group," who would allegedly wage ""phising":/memes/phishing campaigns against victims by "impersonating potential job applicants, and posted links to malware on Facebook and Twitter."
Search Interest
External References
[1] ArsTechnica – 10000 Windows computers may be infected by advanced NSA backdoor
[2] Wikipedia – DoublePulsar
[3] Twitter – @MalwareTechBlog
[4] MalwareTechBlog – How to Accidentally Stop a Global Cyber Attacks
[5] The Hacker News – WannaCry Kill Switched
[6] Kaspersky Lab – WannaCry – Are you safe?
[7] Twitter – Cyber attack cripples UK hospitals
[8] Reddit – /r/worldnews
[9] Reddit – /r/YouShouldKnow
[10] Reddit – /r/pcmasterrace
n13. The Verge – US charges North Korean man in Sony hack and WannaCry ransomware attack
[14] Fast Company – Park Jin Hyok is the North Korean man charged with hacking Sony and Wa
Share Pin